Module 3: Technologies
Module 3 Hands-on Activity
Overview
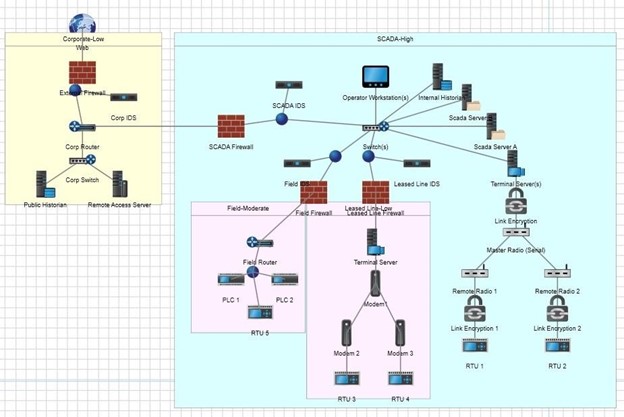
Explore the interactive graphic Secure Architecture Design. This secure design is the result of an evolutionary process of technology advancement and increasing cyber vulnerability presented in the Recommended Practice document Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.
Hands-on Activity Objectives
| Module 3 Learning Objective # | Revised Bloom’s Taxonomy | Hands-On Activity Objectives |
|---|---|---|
| 3.4 | Understand | Discuss the unique challenges/characteristics of devices associated with industrial control systems. |
| 3.5 | Understand | Explain how existing network administration principles can be applied to secure CIKR. |
Assignment
Examine an enterprise diagram for an overview of a network located at Secure Architecture Design. Hover over the various areas of the Secure Architecture Design graphic and click inside the box for additional information associated with the system elements.
After downloading and reading Recommended Practice: Improving Industrial Control Systems Cybersecurity with Defense-In-Depth Strategies (see Required Reading), navigate through the embedded description in the Secure Architectural Design diagram.
Write a short paper describing the following recommended practices for improving industrial control systems cybersecurity with Defense-In-Depth Strategies for your team’s fictitious sector-based company:
- Security Challenges within Industrial Control Systems
- Isolating and Protecting Assets: Defense-in-Depth Strategies
- Recommendations and Countermeasures
Grading Criteria Rubric
- Content
- References
- Use of American Psychological Association (APA) style in writing the assignment
Grade points: 100

